SOC-2 Without the Panic: Mapping EDI Controls to Trust Services Criteria


If you manage EDI operations or compliance for a healthcare payer, the words "SOC-2 audit" can feel overwhelming. But navigating SOC-2 for EDI doesn’t need to induce panic, especially when you shift away from spreadsheets and outdated manual processes. The real crisis isn’t the audit itself; it’s what’s lurking behind manual EDI monitoring: hidden costs, SLA penalties, resource drains, and revenue-impacting failures. We know this because, at EDI Sumo, we see firsthand how efficient mapping between EDI controls and SOC-2 Trust Services Criteria (TSC) transforms not just audit outcomes but daily business performance for payers like you.
EDI Monitoring: The True Cost of Staying Manual
If you’re still relying on spreadsheets for EDI monitoring, the repercussions go much deeper than missed checkboxes. Let’s look at the facts that drive up costs and keep your IT teams in a constant state of firefighting:
- Human Error: Spreadsheets are not built for real-time or complex error checks. Missed files and formula mistakes creep in, introducing the risk of missed eligibility enrollments or delayed claims.
- Visibility Gaps: When failures or delays go unnoticed, SLA penalties rack up quietly. Many health plans absorb 15-20% in preventable penalties just because issues are found too late, if at all.
- Resource Drain: IT teams waste hours (sometimes 40% of their week) resolving exceptions by hand, leaving little time for strategic projects or innovation.
- Revenue Loss: Unnoticed aging pages (process bottlenecks where files remain stuck) directly translate into lost revenue since unenrolled or unprocessed claims cannot be billed or paid.
Trust Services Criteria: Why They Matter for Every EDI Process
The backbone of SOC-2 is the Trust Services Criteria, which apply directly to the way your organization processes, secures, and delivers EDI files. For healthcare payers, certain criteria have a direct impact on both compliance and operations:
- Security (CC Series): Ensures only authorized users access EDI files.
- Confidentiality: Critical for HIPAA, safeguarding PHI in 834/837 EDI files during transfers and at rest.
- Availability: Relates to uptime and file transfer monitoring. If you miss a trading partner’s file, you miss revenue.
- Processing Integrity: Ensures claims and eligibility data are complete, accurate, and processed on time. Misses here often stem from outdated spreadsheet-based checks.
What does this mean? If your EDI monitoring can’t directly produce evidence for each of these, you are not just risking a poor audit outcome; you’re guaranteeing higher operating costs and more pressure on your IT and operations teams.
Step-By-Step: Mapping EDI Controls to SOC-2 Criteria Without Losing Sleep
Here’s our approach, refined for real-world healthcare payer operations, not just for compliance but for business value:
1. Identify Which Trust Services Criteria Apply
- Start with Security: This is non-negotiable for EDI since access control ensures only the right users handle claims and enrollment data.
- Add Confidentiality if you touch PHI.
- Prioritize Availability and Processing Integrity if your contracts have tight SLAs or if claims rejections mean revenue hits.
Always review customer contracts and partner requirements. Many payers require real-time eligibility checks or 24/7 file receipt, which means those TSCs must be covered by robust, auditable controls, not by after-the-fact spreadsheet audits.
2. Build Your EDI Control Matrix (Without Relying on Spreadsheets)
Break down your EDI processes and map where you currently stand. Building this matrix in a platform or tool that can support real-time monitoring and reporting will save you days during an audit:
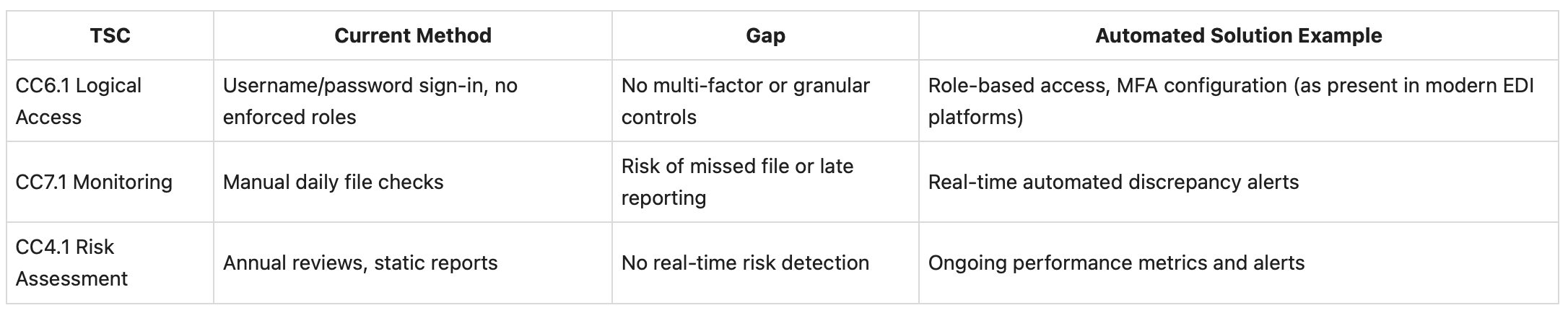
3. Map Automated EDI Controls Directly to Each TSC
For each gap, define an automated (not manual) control. For instance, if you frequently discover missed files too late because your spreadsheet only updates once a day, your control should include automated SFTP monitoring with real-time alerts. This direct automation is also what makes evidence collection effortless come audit time.
- Automated SLA alerts tie to Availability TSC and eliminate undetected missed files—no more aging pages hiding failed transactions.
- Custom validations tied to WEDI/SNIP levels directly support Processing Integrity by flagging errors before they cost you revenue or client trust.
- Audit trails (file movement, access logs) and automated encryption reporting are ready-made for Security and Confidentiality.
- Multi-format support and unified dashboards put ongoing compliance back in the hands of business users, freeing up IT for higher-value work.

4. Document as You Go: Make Audit Evidence Part of Everyday Work
Your goal is to eliminate frantic evidence collection sprints. Screenshots of unified dashboards, exported error logs, and system-generated uptime records are all gold for auditors. The key is to make this documentation automatic, not a manual scramble days before the audit window closes. Regular quarterly review of your EDI environment (especially as standards and requirements evolve) means no more last-minute surprises or outdated process documents.
Why Manual Exception Handling Is the Enemy of Both IT Teams and Compliance
We’ve seen IT teams lose 40% of their EDI support hours chasing down exceptions and coding spreadsheet macros or fixing missed enrollments by hand. This manual burden is the silent killer of operational progress. With the right platform approach, exception handling (including failed 837 claims, missing 834 enrollments, or stuck 277s) becomes automatic, actionable, and reportable. No more daily emails chasing down discrepancies or combing through logs, just in case an issue was missed.
This is where the real EDI transformation happens. By eliminating manual exception handling, you not only close the audit gap but also unlock significant efficiency and cost reduction within your IT and operations teams, empowering them to work on transformation, not just firefighting.
Missed Files = Missed Revenue: Why Aging Pages Can’t Hide
Too often, payers discover hidden EDI failures buried deep in aging pages of manual reports. Each missed file or aging transaction isn’t just a compliance liability; it’s a direct revenue hit. Enrollment files not loaded, claims not submitted, 277s not returned all result in lost payments, increased denials, and even client churn. The impact compounds over time for each unnoticed failure.
- Automated monitoring means every file, every format, and every transaction is tracked in real-time, with exceptions surfaced instantly.
- No more surprises: Errant files or delayed reports simply cannot slip through the cracks or get lost in spreadsheet chaos.
- Revenue assurance: Consistent, automated EDI tracking assures that every valid enrollment or claim can be billed efficiently, speeding cash flow.
This is the foundational pillar for not just compliance, but also operational predictability and profitability in healthcare payer environments.
SLA Penalties: The Hidden Drain in Health Insurance EDI
If you ever wondered where a chunk of your operating budget goes each year, check the cost of SLA penalties from missed EDI files or delayed processing. Spreadsheet-based workflows almost guarantee that some issues go undetected until after deadlines pass and penalties are assessed. Even a 1% miss rate in a high-volume environment can mean tens or hundreds of thousands in lost margin annually.
Automated reporting and proactive alerts ensure that breaches are identified and addressed before penalties hit. This approach not only gives you proof for external SOC-2 assessors but, more importantly, supports a culture of continuous improvement where SLA misses become rare exceptions, not annual line items.
Make EDI Audit Readiness Routine, Not a Fire Drill
SOC-2 panic is rooted in the unknown: The fleeting chance that evidence won’t be retrievable, or that a missed SLA will surface at the worst time. When your EDI controls are directly mapped to SOC-2 Trust Services Criteria, and evidence is generated as a natural byproduct of your workflow, compliance becomes a routine state, not a scramble.
Real audit wins happen when:
- Dashboards show historical uptime, error, and access logs that can be exported in minutes
- Screenshots, performance metrics, and audit logs are continually collected and reviewed
- No single missed file or exception can go unaddressed or unreported
Whether you are a CIO, EDI Director, or Claims Management Director, this means you can walk into your SOC-2 review confident that every process is defensible and every TSC is backed by living, breathing evidence.
Want to Go Deeper? More Resources for EDI Leaders
- How Automated EDI Monitoring Streamlines SOC-2 Compliance and Reduces Audit Stress
- Why Healthcare EDI Monitoring Solutions Fall Short and How to Bridge the Gaps
Turn EDI Anxiety Into Audit-Ready Confidence
We’ve seen organizations recapture IT capacity, reduce SLA penalty payouts, and eliminate operational blind spots by trading spreadsheet chaos for real automation and visibility.
If you’re ready to ditch manual EDI exception handling and see what panic-free compliance actually looks like, connect with us at EDI Sumo. We’re happy to share our perspective, walk through your current EDI landscape, and show you exactly how to make seamless SOC-2 audit readiness your new normal.


.png)





.png)

.png)


.png)
